|
A tool to help ransomware victims find which family and sub-version of ransomware has encrypted their data and then get the appropriate decryption tool, if it exists. Are your computer affected by Ransomware? Ransomware has grabbed the world attention ever since 2014. While most ransomware attacks can’t be defeated, Bitdefender constantly creates and updates ransomware decryption tools for families that have either vulnerable encryption algorithms or for which a master decryption key has been leaked. This tool analyzes both the ransom note and the encrypted file samples to identify the strain of ransomware and suggest a decryption tool for the identified family, if such a tool is available. Step 1 Download the BRR tool and save it somewhere on your computer. The latest version is always available here: This tool requires an active internet connection.
Step 2 Run the BDRansomRecognitionTool.exe and allow it to execute if prompted by an UAC alert. Step 3 Read and agree to the End User License Agreement. Step 4 The application has two fields to fill in: Choose the path to the ransom note file or the path to a folder containing encrypted files. You can choose either option, but the tool needs at least one of the pieces of information to detect which strain of ransomware has encrypted your information. If none of the fields are filled in, you cannot proceed any further Step 5 Press Scan. The application gives a warning if the ransom-note path is not filled in, as the detection accuracy is slightly lower in this case. The content of the ransom note is submitted for analysis to Bitdefender cloud. If the user provides any encrypted file, NO file content will be submitted to our cloud, as the tool only analyzes the filename and its extension. If the ransomware family cannot be identified, the user is informed about this. In some cases, multiple families of ransomware display similar features. In this case, the Bitdefender Ransomware Recognition tool displays the possible ransomware families next to an indicator of confidence. Usually the first result is the most relevant and it is displayed with the highest confidence percentage (the one with the highest percentage). If the ransomware has an associated DecryptionTool, a link is provided in the Decryptor column. Good news for system administrators! If you need to run this tool on multiple computers, please use it via command line by passing it the following parameters: -note:RANSOM_NOTE_LOCATION; -test:ENCRYPTED_FILES_LOCATION; Test cases : BDRansomRecognitionTool.exe -note:C:\temp\decrypt_my_files.html; -test:C:\encrypted; BDRansomRecognitionTool.exe -note:C:\temp\decrypt_my_files.html; BDRansomRecognitionTool.exe -test:C:\encrypted; At least one of the parameters above needs to be passed to the tool and end in “;”. Also, any path provided must be absolute. Disclaimer: This tool is developed and offered by Bitdefender, we are listing this additional tool for the purpose of finding solution to decrypt your ransomware-infected Windows based computer. We do not guaranteed for any result and do not take any responsibility or technical support.
Reported by Bitdefender Intelligence, from September 2017 until February 2018,
Ransomware reports have followed a descending curve, while coin miner reports have increased by 130 percent by January 2018. Interestingly, cryptojacking is currently one of the fastest spreading cyber threats, already outranking ransomware’s exposure by a factor of 1 to 100 according to Bitdefender’s intelligence, and is recently displaying targeted behavior, by leveraging fileless techniques and exploits to infiltrate organizations and spread laterally. 
Cryptocurrency mining is a very recent attack wave that spurred in September 2017 and has since been ranked the single biggest cyberthreat of the moment. Crypto jacking is currently one of the fastest spreading cyber threats, already outranking ransomware’s exposure by a factor of 1 to 100 according to Bitdefender’s intelligence, and is recently displaying targeted behavior. Attacks such as WannaMine leverage file less technique and exploits to infiltrate organizations and spread laterally, and even to the point of reaching critical infrastructures.
Ransomware has been notoriously causing serious security concerns, especially when weaponized using government-developed cyber weapons, such as the WannaCry incidents, generating billions of dollars in revenue for cybercriminals.
While cryptocurrency was the main currency for ransomware, everything changed when Bitcoin’s value surged up to $20,000 per unit, making threat actors think of new ways of mining for virtual currencies, as it was more profitable that ransomware. The emergence of browser-based mining clients, such as CoinHive, has spurred a new frenzy of threats, as cybercriminals identified a new, more efferent, and more profitable way generate review.
While the common belief is that only endpoints are facing this mounting threat, threat actors in need of increased computing power and resources have been gunning for data center, as they are more lucrative from a mining point of view. A successful attack on a data center in terms of successfully planning cryptocurrency mining software, can generate a huge revenue for threat actors even it lasts for a mere couple of hours before being detected.
Unfortunately, new cryptojacking attacks embed stealth tactics, which means it takes a long time for them to be detected, while they can cause a huge surge in bills for companies that rely use infrastructure-as-a-service offerings with automatic resource provisioning, such as Azure, AWS or Google Cloud Platform services. For more information about how ransomware and coin miners have evolved over the past couple of months and how data centres are affected, check out the latest “Cryptocurrency Mining Craze Going for Data Centers” whitepaper. To understand the rapid evolution of mining attacks and what risks they can pose for your businesses and infrastructure, particularly if you are running a data center or cloud instances, please watch this webinar hosted by IDC and Bitdefender. Hosted by Alexei Proskura, Program Director, Security, IDC CEE and Liviu Arsene, Senior Global Cyber Security Analyst, Bitdefender, you’ll also gain insights on how to protect your organization from cryptojacking. Sing up for the webinar!
News sourced from Bitdefender
Firms that didn’t patch and enabled local admin rights continue to suffer post cyber-attack7/17/2017
By Graham Cluley on Jul 12, 2017 |
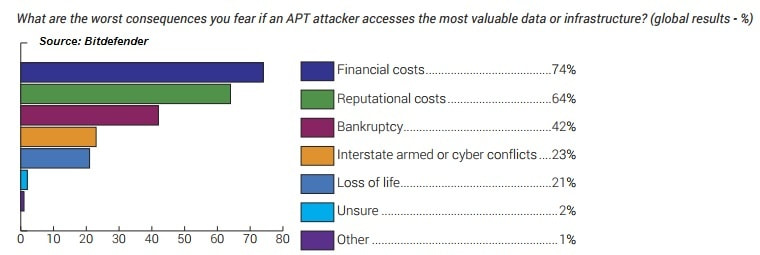
Here’s a salutary reminder for all businesses. Just because a malware outbreak has begun to fade away from the newspaper headlines, doesn’t mean your troubles are over. Many firms can continue to suffer long afterwards. In late June, a malware attack crippled businesses and critical infrastructure in Ukraine at astonishing speed. Initially suspected of being a similar ransomware attack to the WannaCry outbreak seen the month before, the malware (variously named as Petya, NotPetya or GoldenEye by security vendors) appears to have been launched through a malicious automatic update to a popular Ukrainian accounting software tool called MeDoc. We tell companies all the time to keep their software updated with the latest available patches, and yet here was an update which actually delivered a devastating malware attack. The irony isn’t lost on anybody. By Razvan Muresan on Jul 17, 2017 | Some 75 percent of US CISOs state the worst consequences of an attacker gaining access to their companies’ most valuable asset would be the financial cost and reputational damage. However, few say the financial cost could lead to bankruptcy 35%. In Sweden, 65 percent of those surveyed expect cyber criminals accessing prized assets could lead to the downfall of the company. Reputational costs are perceived most as a main threat in the UK, where almost 80 percent of respondents have mentioned it as the most dangerous risk to their business, almost triple the percentage of Italian IT execs.
Even if it sounds alarming, loss of life – mentioned by 39 percent of the Swedes - is a severe yet real consequence of an APT. Targeted attacks could also aim at critical national or transnational infrastructures (i.e. nuclear power plants, national energy grids, urban water supplies, transportation management systems, traffic controller systems, hospitals and other healthcare facilities). In a modern environment where automation has become a reality, targeted attacks can practically paralyze countries and, unfortunately, lead to human casualties. By Razvan Muresan on Jun 15, 2017 |
Attackers are now targeting small and medium businesses to extort higher fees, a Bitdefender survey shows, meeting the company’s predictions for 2017. One in five small and medium businesses (SMBs) in the US reported a ransomware attack within the past 12 months, according to a Bitdefender survey of 250 IT pros in the US working in SMBs, carried out by Spiceworks. Some 38% indicated they paid ransom - $2,423 on average - but most did not recover the encrypted data. Ransomware, a type of malware that locks and usually encrypts a computer’s files until the victim pays to regain access, is the fastest growing malware threat, targeting users of all types—from the home user to the corporate network. On average, more than 4,000 ransomware attacks have occurred daily since January 1, 2016, a 300-percent increase over the approximately 1,000 attacks per day seen in 2015, according to the U.S. Department of Justice. SMBs are ideal targets for ransomware developers as some do not invest in security solutions, yet they handle sensitive business information (i.e. customer data, financial records, product info), targets that cyber-criminals value most. Bitdefender’s survey shows that less than half (45%) of the SMBs that paid to regain access to their data after falling victim to ransomware actually got their information back. From those targeted, most were able to mitigate the attack by restoring from backup (65%) or through security software/practices (52%). A quarter of those targeted couldn’t find a solution to address the ransomware attack and lost their data. |
Protect from RansomwareBuy Bitdefender now RECOMMENDED READINGs
All
|
For BUSINESS: Gravityzone Advanced Business Security
We are a certified Sales Partner (more than 8 years), not principal
Copyright © 2024 We are a Gold Partner of Bitdefender.
Website managed by 57Network.com




 RSS Feed
RSS Feed
