|
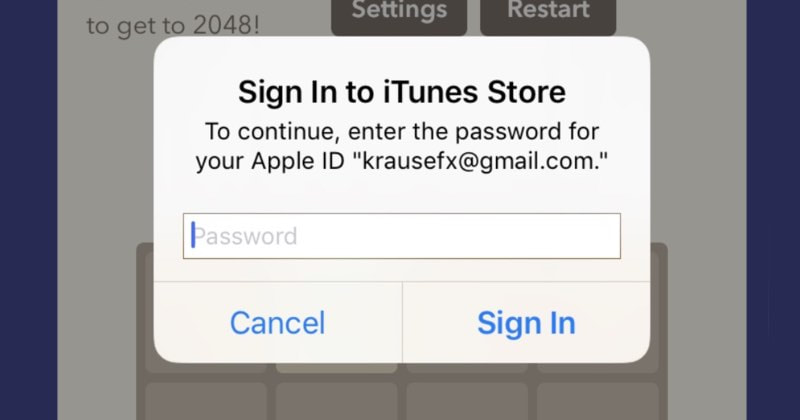
It’s all too easy for a malicious app developer to determine a user’s Apple ID password – just by asking for it.
Developer Felix Krause warns users to be on their guard against password-stealing apps that dupe users into entering their sensitive passwords by using fake login dialogs disguised as legitimate requests from the underlying iOS operating system. The problem lies in the fact that with just a few lines of code, a third-party app developer can pop up a password prompt that looks identical to a legitimate one created by iOS. By Razvan Muresan on Aug 22, 2017 |
Some 90 percent of boards of directors in the US address cybersecurity as a serious risk management issue with severe reputation and financial consequences, while only 8 percent haven’t done it so far, according to a recent Bitdefender survey. Some 60 percent of IT security decision makers in the US say their companies could ‘definitely’ be a target of cyberespionage campaigns using advanced persistent threats (APTs), according to a recent survey by security firm Bitdefender. These complex cyber tools are crafted for high-profile entities and operate by silently gathering sensitive data over long periods. Another 35 percent of respondents say their IT infrastructure could ‘possibly’ be targeted in high-level cyberespionage actions that exfiltrate intelligence systematically. By Filip Truta on Aug 16, 2017 |
Organizations worldwide are on track to spend a cumulative $86.4 billion on information security products this year, a 7 percent increase over 2016, Gartner reports. The research firm anticipates that figure will climb to $93 billion in 2018. The IT-focused advisory firm projects fast growth for the security testing market. Despite the relatively small base, the infrastructure-protecting segment continues to suffer data breaches, fueling demand for application security testing. “Spending on emerging application security testing tools, particularly interactive application security testing (IAST), will contribute to the growth of this segment through 2021,” says Gartner. Firms that didn’t patch and enabled local admin rights continue to suffer post cyber-attack7/17/2017
By Graham Cluley on Jul 12, 2017 |
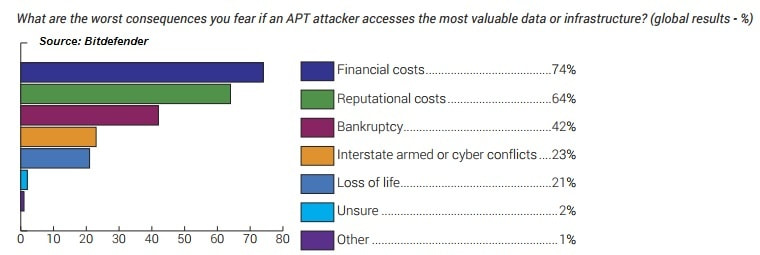
Here’s a salutary reminder for all businesses. Just because a malware outbreak has begun to fade away from the newspaper headlines, doesn’t mean your troubles are over. Many firms can continue to suffer long afterwards. In late June, a malware attack crippled businesses and critical infrastructure in Ukraine at astonishing speed. Initially suspected of being a similar ransomware attack to the WannaCry outbreak seen the month before, the malware (variously named as Petya, NotPetya or GoldenEye by security vendors) appears to have been launched through a malicious automatic update to a popular Ukrainian accounting software tool called MeDoc. We tell companies all the time to keep their software updated with the latest available patches, and yet here was an update which actually delivered a devastating malware attack. The irony isn’t lost on anybody. By Razvan Muresan on Jul 17, 2017 | Some 75 percent of US CISOs state the worst consequences of an attacker gaining access to their companies’ most valuable asset would be the financial cost and reputational damage. However, few say the financial cost could lead to bankruptcy 35%. In Sweden, 65 percent of those surveyed expect cyber criminals accessing prized assets could lead to the downfall of the company. Reputational costs are perceived most as a main threat in the UK, where almost 80 percent of respondents have mentioned it as the most dangerous risk to their business, almost triple the percentage of Italian IT execs.
Even if it sounds alarming, loss of life – mentioned by 39 percent of the Swedes - is a severe yet real consequence of an APT. Targeted attacks could also aim at critical national or transnational infrastructures (i.e. nuclear power plants, national energy grids, urban water supplies, transportation management systems, traffic controller systems, hospitals and other healthcare facilities). In a modern environment where automation has become a reality, targeted attacks can practically paralyze countries and, unfortunately, lead to human casualties. By Razvan Muresan on Jun 15, 2017 |
Attackers are now targeting small and medium businesses to extort higher fees, a Bitdefender survey shows, meeting the company’s predictions for 2017. One in five small and medium businesses (SMBs) in the US reported a ransomware attack within the past 12 months, according to a Bitdefender survey of 250 IT pros in the US working in SMBs, carried out by Spiceworks. Some 38% indicated they paid ransom - $2,423 on average - but most did not recover the encrypted data. Ransomware, a type of malware that locks and usually encrypts a computer’s files until the victim pays to regain access, is the fastest growing malware threat, targeting users of all types—from the home user to the corporate network. On average, more than 4,000 ransomware attacks have occurred daily since January 1, 2016, a 300-percent increase over the approximately 1,000 attacks per day seen in 2015, according to the U.S. Department of Justice. SMBs are ideal targets for ransomware developers as some do not invest in security solutions, yet they handle sensitive business information (i.e. customer data, financial records, product info), targets that cyber-criminals value most. Bitdefender’s survey shows that less than half (45%) of the SMBs that paid to regain access to their data after falling victim to ransomware actually got their information back. From those targeted, most were able to mitigate the attack by restoring from backup (65%) or through security software/practices (52%). A quarter of those targeted couldn’t find a solution to address the ransomware attack and lost their data. By Razvan Muresan on May 16, 2017 |
Ransomware infections impact individual users and businesses, regardless of size or industry, by causing service disruptions, financial loss and, in some cases, permanent loss of valuable data. In 2016, the number of ransomware attacks increased 300 percent from 2015, with over 4,000 attacks detected per day, according to US government statistics. WannaCryptor (WannaCry), the most recent version of ransomware, has targeted businesses in more than 70 countries around the world, with more than 250,000 infected terminals so far. By late Monday, cybersecurity officials said the globe-spanning WannaCry cyberattack had largely been contained, though governments and companies are likely to continue disclosing instances of infection for days or weeks as they get a better handle on the scope of the attack, the WSJ reports. The FT reports that "at least a dozen other NSA tools are currently being discussed and worked on as the basis of potential new cyber weapons on hacking forums on the dark web." |
Protect from RansomwareBuy Bitdefender now RECOMMENDED READINGs
All
|
For BUSINESS: Gravityzone Advanced Business Security
We are a certified Sales Partner (more than 8 years), not principal
Copyright © 2024 We are a Gold Partner of Bitdefender.
Website managed by 57Network.com


 RSS Feed
RSS Feed
