|
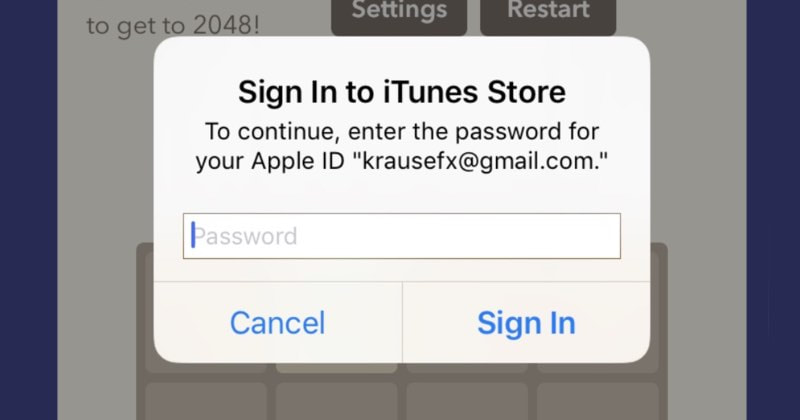
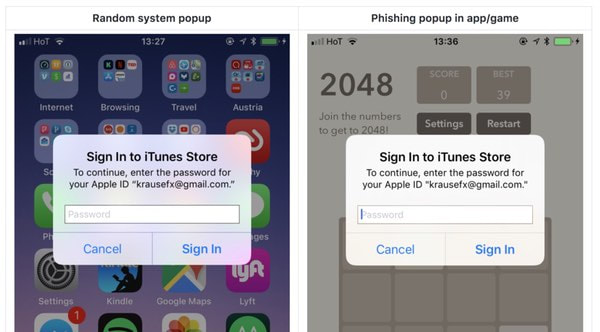
It’s all too easy for a malicious app developer to determine a user’s Apple ID password – just by asking for it. Developer Felix Krause warns users to be on their guard against password-stealing apps that dupe users into entering their sensitive passwords by using fake login dialogs disguised as legitimate requests from the underlying iOS operating system. The problem lies in the fact that with just a few lines of code, a third-party app developer can pop up a password prompt that looks identical to a legitimate one created by iOS. The problem, says Krause, is compounded by the regularity that iOS users can be asked to enter their passwords for legitimate reasons – such as installing an operating system update:
“As a result, users are trained to just enter their Apple ID password whenever iOS prompts you to do so. However, those popups are not only shown on the lock screen, and the home screen, but also inside random apps, e.g. when they want to access iCloud, GameCenter or In-App-Purchases.” “This could easily be abused by any app, just by showing an UIAlertController, that looks exactly like the system dialog.” So there’s the problem. How are you supposed to tell the difference between a genuine pop-up and one initiated by a password thief? One approach is to give users a way to uniquely customise iOS’s password dialogs. That’s an approach taken by some banking apps, which give account owners the option of choosing their own “Welcome” message that will be displayed alongside the login screen in an attempt to make it less likely that they will enter their credentials into a malicious app. So, rather than your app saying “Hi” or “Welcome” you could change it to something that malicious hackers would find less predictable like “Greetings Galactic Lord President” or “Beetroot!”. If you didn’t see the custom message you normally expect to see, you know something fishy (phishy?) is afoot. Alternatively some banking apps allow you to add a personal photograph to the login page. If it’s not displayed (or if the photo is not the one you chose) then you know not to enter yoru credentials. Wouldn’t it be possible for iOS to implement something similar to this? The good news is, as Krause told The Register, there don’t seem to be any reports that any apps have been using the phishing technique in the wild. However, it does strike me that we are reliant on Apple spotting any offending apps which attempt this phishing trick before they manage to get into the official App Store. Wouldn’t we all feel a little more safer if the operating system itself made it trickier to forge a convincing-looking password prompt? Source: Hot for Security powered by Bitdefender Comments are closed.
|
Protect from RansomwareBuy Bitdefender now RECOMMENDED READINGs
All
|
For BUSINESS: Gravityzone Advanced Business Security
We are a certified Sales Partner (more than 8 years), not principal
Copyright © 2024 We are a Gold Partner of Bitdefender.
Website managed by 57Network.com

 RSS Feed
RSS Feed
