|
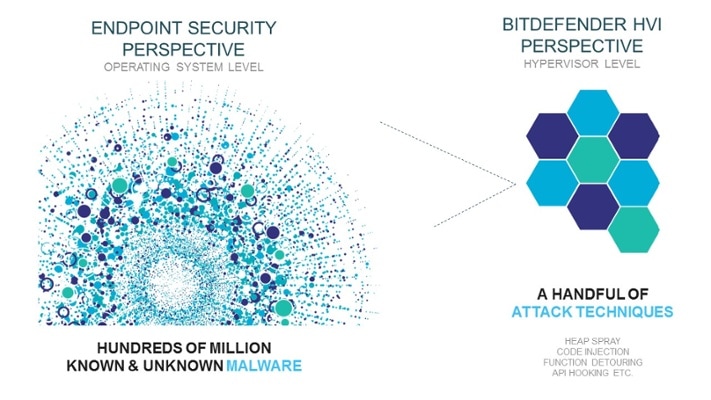
By Deepak Patel on Mar 22, 2017 | Recent surveys have revealed that 34 percent of companies have been breached in the past 12 months alone, with 74 percent of IT decision makers claiming they have little to no clue as to how the breach occurred. Advanced threats targeting organizations often use custom-made and target-specific attack patterns to greatly increase not only their infiltration success but also their persistence. With each threat being unique for every organization, traditional signature-based approaches for blocking attacks lack the ability to be truly proactive with never-before-seen malware samples. However, if malware can be easily obfuscated or repacked to dodge traditional security mechanisms, the attack techniques employed by advanced attacks are few, and they often remain the same. A truly innovative security technology should be able to focus on identifying those attack techniques, rather than the malicious payloads. That way, even if the sample has never been seen before, the technique will often betray the intent of an attack. Traditional Security Focuses on Malicious Payloads Security technology for traditional endpoints – whether virtual of physical - often use mechanisms to detect attacks based on whether the malicious payload has been seen before or whether it’s behavior is suspicious. While this prevents the infected file from executing or plugs an application when its behavior becomes malignant, advanced threats targeting businesses and other organizations often rely on zero-day vulnerabilities for delivering those payloads undetected onto a victim’s computer. It’s because of these zero-day vulnerabilities that advanced attacks often succeed in infecting victims, as they usually allow the attacker to “smuggle” a previously unknown malicious payload that can execute - sometimes with elevated privileges – without triggering alerts from traditional endpoint security tools. In hybrid infrastructures, an advanced threat could affect multiple VM instances by jumping from one VM to another while evading traditional in-guest security mechanisms. Focusing on the “How” Instead of the “What”Traditional security technologies focus on the “What” (e.g. type of file, type of malware, type of behavior). A different approach that could address the problem of advanced threats lies in understanding “How” they operate. While advanced threats vary in complexity, behavior, and even attack vectors, malicious actors usually resort to one of a handful of tricks to gain control of a machine. To elevate privileges or to hide a malicious application’s execution within a legitimate thread, few techniques are normally employed. Buffer overflow, heap spray, code injection, and function detouring are some examples. All these advanced attacks operate at the memory level, meaning that sometimes there’s no file for the traditional security solution to analyze. Some memory corruption attacks that sometimes take the form of zero-day vulnerabilities in popular applications (e.g. Flash, Adobe, Java). They could be as simple as a couple of lines of code that alter how memory is allocated within a legitimate application to place malicious instructions. These events can sometimes be “invisible” to traditional security solutions, as they can’t interact with raw memory. Vital to defending against targeted attacks is an understanding of “How” changing the order in which some functions are executed within a legitimate application can radically affect its behavior. However, knowing “How” advanced threats operate is only part of the solution. You still need an “outside observer” – in this case, a technology outside the guest operating system – to assess how those techniques impact the raw memory associated with each VM. Citrix XenServer Meets Bitdefender Hypervisor IntrospectionCitrix’s XenSever is the perfect example of how virtualization technology and security technology can work together to offer an unprecedented level of insight into “How” advanced targeted threats try to compromise a victim, while at the same time having minimum impact on the performance of the guest VM.
Leveraging Citrix’s XenServer Direct Inspect APIs, Bitdefender’s Hypervisor Introspection technology can work directly with the raw memory stack of each guest VM and read unaltered information, without relying on information from the guest’s OS. In addition to detecting all types of kernel-mode or user-mode malware, zero-days vulnerabilities aiming to drop any form of malicious payload will also be plugged, as hypervisor introspection identifies the attack technique and prevents the attacker from ever delivering a payload. Whether it’s an entire virtual infrastructure built on XenServer or just a couple of servers in a data center, Bitdefender Hypervisor Introspection can augment in-place security technologies, regardless of what security solution is running inside guest VMs. The simplicity and seamless deployment enable IT decision makers to significantly improve their infrastructure’s security against any type of advanced targeted attack, as it can block attacks in real-time, at the hypervisor level. Fast, accurate, and truly agentless, Bitdefender Hypervisor Introspection technology can also insert a temporary remediation tool within an infected VM to dispense with the threat before it inflicts any damage. The top three fears that IT decision makers used to face – detection, prevention, and remediation – when faced with advanced targeted threats, can now be solved with this new and revolutionary security layer. Source: Bitdefender Business Insight in Virtualisation and Cloud Security Comments are closed.
|
Protect from RansomwareBuy Bitdefender now RECOMMENDED READINGs
All
|
For BUSINESS: Gravityzone Advanced Business Security
We are a certified Sales Partner (more than 8 years), not principal
Copyright © 2024 We are a Gold Partner of Bitdefender.
Website managed by 57Network.com

 RSS Feed
RSS Feed
